v8.3 and later
Overview
To authenticate users in Cora SeQuence using claims-based authentication, you need to modify the web.config file for each Cora SeQuence site (Windows Services are not required). There are two procedures to perform.
- IIS
- web.config file
Prerequisites
- You must configure all Cora SeQuence sites under HTTPS. For more information, see Configure HTTPS for Sequence Sites.
- Verify that your security token service (STS) supports SAML 2.0, and has a WS-Federation Endpoint.
IIS Procedure
- Configure the root level authentication for each Cora SeQuence site.
Setting Value Anonymous Authentication Enabled ASP.NET Impersonation Enabled Windows Authentication Disabled - For the Default Document, add the
Default.aspxfile for each Cora SeQuence site.
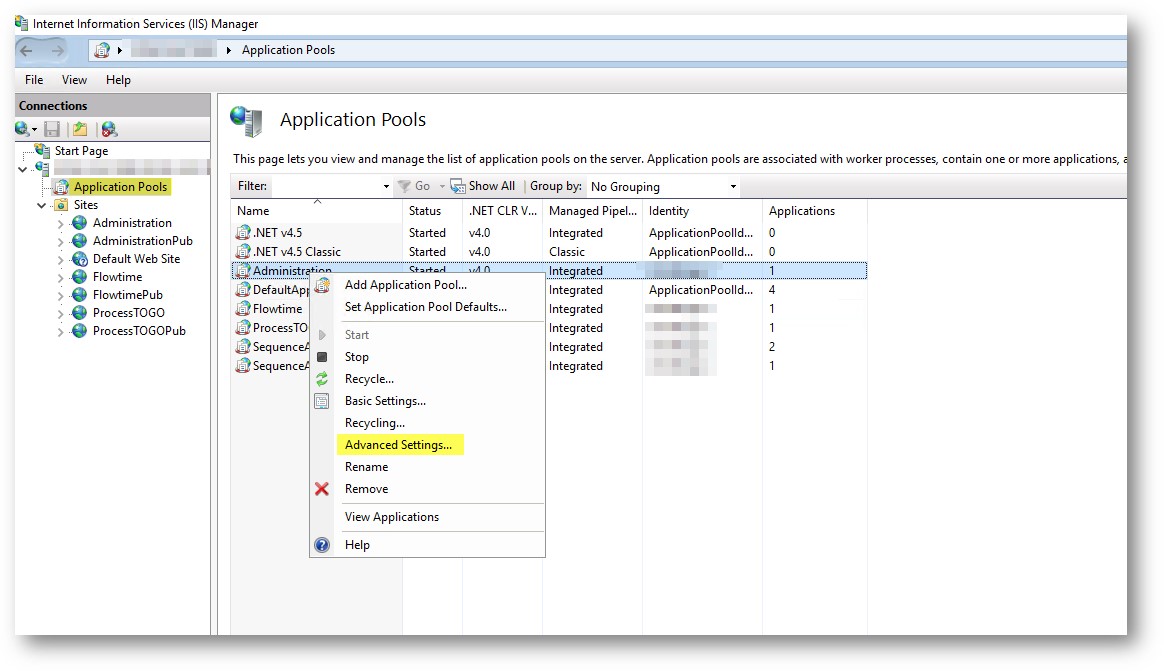
TheDefault.aspxfile must be the only document. - In the Connections panel, select Application Pools.
- Right-click the application pool used by your application and select Advanced Settings.
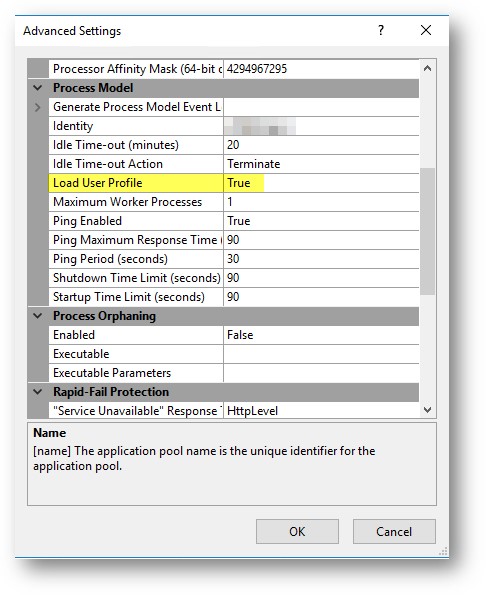
- In the Process Model section, set the Load User Profile attribute to True.
web.config File Procedure
- Add the
system.identityModelandsystem.identityModel.servicessection declarations to the<configSections>section.<section name="system.identityModel" type="System.IdentityModel.Configuration.SystemIdentityModelSection, System.IdentityModel, Version=4.0.0.0, Culture=neutral, PublicKeyToken=B77A5C561934E089"/> <section name="system.identityModel.services" type="System.IdentityModel.Services.Configuration.SystemIdentityModelServicesSection, System.IdentityModel.Services, Version=4.0.0.0, Culture=neutral, PublicKeyToken=B77A5C561934E089"/>
- Replace the
<authentication>section under the<sequence.engine>section, with the code sample in this step.- For claimType, use one of the claim types provided by your STS, which you can match with one of the following Cora SeQuence employees table.
- Domain/User Name
- User Name
- Email
- For authenticationType, use one of the following (depending on your selection from the previous sub-step.
- Enter a unique name for the originalIssuer attribute.
<authentication impersonate="false"> <providers> <add type="PNMsoft.Sequence.Security.ClaimsIdentityAuthenticationProvider, PNMsoft.Sequence.IdentityModel.v8, Version=8.0.0.0, Culture=neutral, PublicKeyToken=0a1a1b90c1c5dca1" /> </providers> <claims enabled="true"> <IdentityClaims> <add claimType="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress" originalIssuer="https://sts.windows.net/yourTenantID/" authenticationType="http://pnmsoft.com/sequence/2008/03/authentication/types/email" /> </IdentityClaims> </claims> </authentication>
- Make sure that you configure the modules for the
<system.identityModel>section under the main<system.webServer><modules>.<add name="SessionAuthenticationModule" type="System.IdentityModel.Services.SessionAuthenticationModule, System.IdentityModel.Services, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" preCondition="managedHandler" /> <add name="WSFederationAuthenticationModule" type="System.IdentityModel.Services.WSFederationAuthenticationModule, System.IdentityModel.Services, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" preCondition="managedHandler" />
- Add the following under the main
<configuration>node.<location path="Authentication/Federation"> <system.web> <httpHandlers> <add verb="GET, POST" path="SignIn.axd" type="PNMsoft.Sequence.IdentityModel.Web.FederationSignInHttpHandler, PNMsoft.Sequence.IdentityModel, Version=8.0.0.0, Culture=neutral, PublicKeyToken=0a1a1b90c1c5dca1" /> </httpHandlers> </system.web> <system.webServer> <handlers> <add name="Authentication" verb="GET, POST" path="Authenticate.axd" type="PNMsoft.Sequence.Web.WSFederationAuthenticationHttpHandler, PNMsoft.Sequence.IdentityModel.v8, Version=8.0.0.0, Culture=neutral, PublicKeyToken=0a1a1b90c1c5dca1" /> </handlers> </system.webServer> </location> <location path="FederationMetadata"> <system.web> <authorization> <allow users="*" /> </authorization> </system.web> </location> - Add the following under the
<configuration></configuration>section.- For
<audienceUris><add value=>use the URL of the Sequence site you are configuring. - For
<trustedIssuers><add...>use the following information.<thumbprint>is the thumbprint of your STS token signing certificate. Make sure there are no spaces, there are no coding errors, and that it is plain text.<name>is the value you used for<originalIssuer>in step 4c.
- For
<federationConfiguration><wsFederation>, use the following information.<issuer>is the sign-in URL of your STS (where users are directed to log in).<realm>and<reply>is the URL of the Sequence site you are configuring.
- For
- Configure Administration and Flowtime, and the ProcessTOGO identity issuer setup using the following settings.
Administration and Flowtime<system.identityModel> <identityConfiguration> <audienceUris> <add value="XXXXX" /> </audienceUris> <issuerNameRegistry type="System.IdentityModel.Tokens.ConfigurationBasedIssuerNameRegistry, System.IdentityModel, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089"> <trustedIssuers> <add thumbprint="XXXXX" name=" XXXXX " /> </trustedIssuers> </issuerNameRegistry> <certificateValidation certificateValidationMode="None" /> </identityConfiguration> </system.identityModel> <system.identityModel.services> <federationConfiguration> <cookieHandler requireSsl="true" /> <wsFederation passiveRedirectEnabled="true" issuer="XXXXX" realm="XXXXX" reply=" XXXXX " requireHttps="true" /> </federationConfiguration> </system.identityModel.services>
ProcessTOGO<system.identityModel> <identityConfiguration> <audienceUris> <add value="XXXXX" /> </audienceUris> <issuerNameRegistry type="System.IdentityModel.Tokens.ConfigurationBasedIssuerNameRegistry, System.IdentityModel, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089"> <trustedIssuers> <add thumbprint="XXXXX" name=" XXXXX " /> </trustedIssuers> </issuerNameRegistry> <certificateValidation certificateValidationMode="None" /> </identityConfiguration> </system.identityModel> <system.identityModel.services> <federationConfiguration> <cookieHandler requireSsl="true" name="SequenceSessionId" hideFromScript="false" /> <wsFederation passiveRedirectEnabled="true" issuer="XXXXX" realm="XXXXX" reply=" XXXXX " requireHttps="true" /> </federationConfiguration> </system.identityModel.services>
- Under the
<system.web>section, replace each of the following sections wherever they exist.<authentication mode="None"/> <identity impersonate="true" /> <authorization> <deny users="?" /> </authorization>


